CloudFlare Pro offers a range of advanced features to help protect your website from DDoS attacks. By fine-tuning the settings, you can better safeguard your site from malicious traffic while ensuring legitimate users can still access it. This guide will walk you through the key settings to adjust for optimal DDoS protection.
Summary of Key Settings for DDoS Protection
| Feature | Purpose | Plan Needed |
|---|---|---|
| Managed Ruleset | Blocks known threats automatically | Pro / Enterprise |
| Custom Rules | Blocks specific IPs, bots, etc. | Free / Pro / Enterprise |
| Rate Limiting | Limits requests to prevent flooding | Free / Pro / Enterprise |
| Bot Fight Mode | Blocks malicious bots | Free / Pro / Enterprise |
| Under Attack Mode | Protects during heavy DDoS attacks | Free / Pro / Enterprise |
1. Enable Managed Ruleset
CloudFlare’s Managed Ruleset is pre-configured to block common attack patterns, including those targeting specific CMS platforms like WordPress or Joomla.
Steps to Enable Managed Rules:
-
Log in to your CloudFlare Dashboard.
-
Select your website.
-
Navigate to Security > Security rules.
-
Under the Web application exploits filter, turn on these rule sets:
-
Cloudflare managed ruleset: Created by the Cloudflare security team, this ruleset is designed to provide fast and effective protection for all your applications. It is frequently updated to cover new vulnerabilities and reduce false positives.
-
Leaked credentials detection: Exposed credentials check rules.
-
It is not necessary to enable the CloudFlare OWASP Core Ruleset, as we already have the OWASP Core Ruleset installed and enabled on our servers.
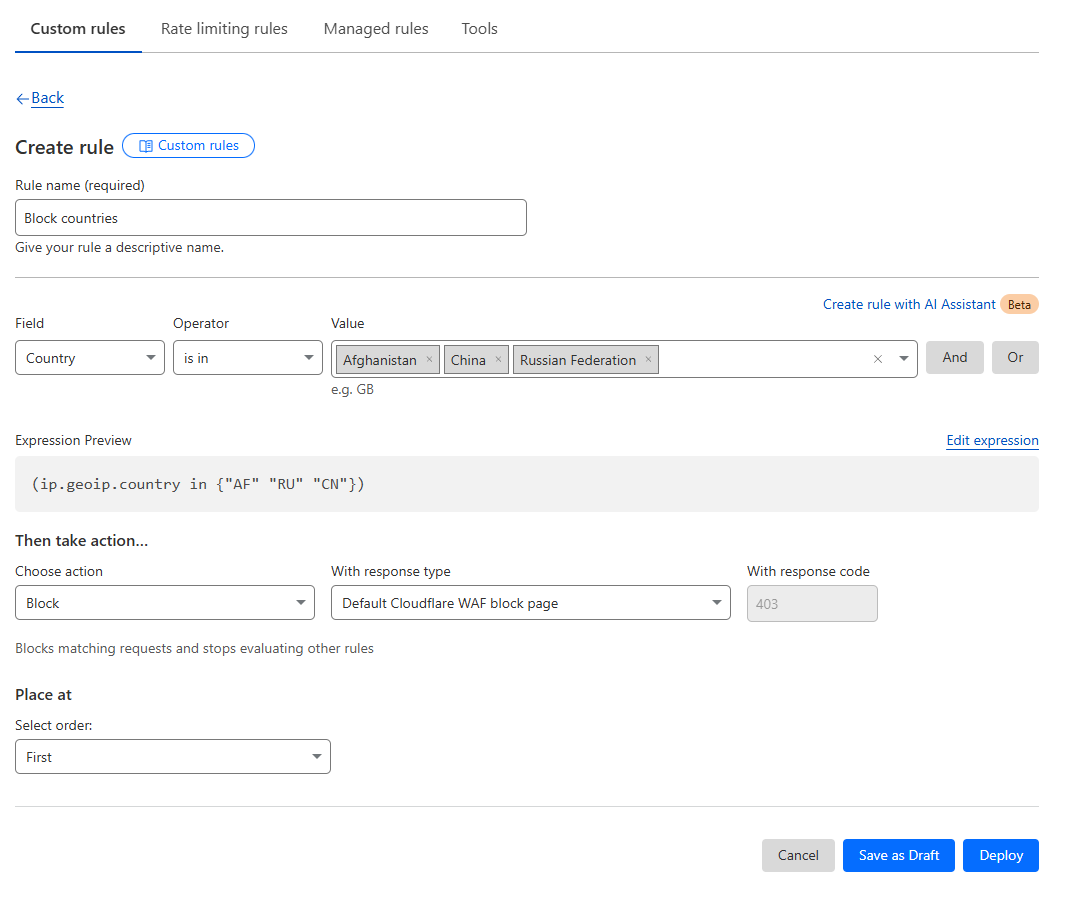
2. Create Custom Firewall Rules
Custom firewall rules allow you to block specific traffic patterns, such as certain IP ranges, countries, user agents, or ASNs (autonomous system numbers).
Steps to Create a Custom Firewall Rule:
-
Go to Security > Security rules.
- Click on the Create Rule button, then on Custom rules.
-
Define the conditions for the rule, such as:
- IP Addresses: Block specific IPs or ranges (e.g.,
192.168.1.0/24). - User Agents: Block malicious bots or scripts by their user agent string.
- ASN: Block traffic from specific networks by ASN.
- Country: Block or challenge visitors from certain countries.
Example Rule to Block a Specific Country:
- Field: Country
- Operator: is in
- Value: [Select the countries]
- Action: Managed Challenge, Block, JS Challenge or Interactive Challenge
- We recommend Managed Challenge if you'd like to let legitimate users to access your page after passing a test, but there is no general rule, as other actions may be more effective for certain types of attacks.
- IP Addresses: Block specific IPs or ranges (e.g.,
-
Click on Deploy to create the rule, then test its impact.
3. Create Rate Limiting Rules
Rate limiting prevents excessive requests from overloading your server. This is especially useful for blocking DDoS attacks targeting specific pages like login forms or APIs.
Steps to Set Up Rate Limiting:
-
-
Go to Security > Security rules.
- Click on the Create Rule button, then on Rate limiting rules.
-
-
Define your rule settings:
- URL Path: Specify the page or endpoint to protect (e.g.,
/wp-login.php). - Threshold: Set the maximum number of requests allowed per minute (e.g., 10 requests per minute).
- Action: Choose to block, challenge, or log the request.
- URL Path: Specify the page or endpoint to protect (e.g.,
-
Save the rule.
4. Enable Bot Fight Mode
Bot Fight Mode helps block malicious bots from interacting with your website. While it is primarily automated, it can be combined with other measures for stronger protection.
Steps to Enable Bot Fight Mode:
-
Go to Security > Settings.
-
Toggle Bot Fight Mode to “On”.
If you have a Pro or Enterprise plan, then Super Bot fight mode will appear instead and it is always enabled. You should consider changing the sub-setting Definitely automated traffic to Blocked or Managed Challenge if your site is overwhelmed by bots and crawlers.
5. Use the IP Access Rules Feature
CloudFlare’s IP Access Rules allow you to block or challenge specific IPs or entire IP ranges.
Steps to Add IP Access Rules:
-
Go to Security > Tools > IP Access Rules.
-
Enter the IP address, range, or ASN to block or challenge.
-
Select the action:
- Block: Completely deny access.
- Challenge: Require visitors to complete a CAPTCHA before accessing your site.
6. Enable Under Attack Mode
When experiencing a heavy DDoS attack, you can enable Under Attack Mode to apply stricter access rules automatically.
Steps to Enable Under Attack Mode:
-
Go to Overview or Security.
-
Toggle Under Attack Mode to “On”.
-
This setting forces visitors to pass an interstitial page (a “checking your browser” screen) before accessing your site.
7. Fine-Tune Caching and CDN Settings
CloudFlare’s caching system helps reduce the load on your origin server by serving content from its CDN. For DDoS attacks targeting specific URLs, increasing the cache duration can help mitigate the impact.
Steps to Adjust Cache Settings:
-
Go to Caching > Configuration > Page Rules.
-
Create a new Page Rule for heavily targeted pages:
- URL Pattern: Specify the page (e.g.,
example.com/wp-login.php). - Setting: Cache Level.
- Value: Cache Everything.
- URL Pattern: Specify the page (e.g.,
-
Save and prioritise the rule.
8. Monitor Traffic Using Analytics
CloudFlare Pro includes real-time analytics to help you monitor traffic patterns and identify unusual spikes.
Steps to Access Analytics:
-
Go to Security > Analytics.
-
Review:
- Top countries by request volume.
- Top IPs generating traffic.
- Top threats blocked by CloudFlare.
-
Use these insights to create or adjust rules.
If the attack has just started, users can set the analytics to display stats for the last 30 minutes to identify trends or spikes in malicious traffic. Over time, broader views like 6 or 24 hours may provide insights into ongoing attack strategies.
9. Enable HTTP/2 and TLS Security Features
Modern protocols like HTTP/2 improve performance and security. Additionally, enabling strict TLS settings can help prevent abuse.
Steps to Enable These Features:
-
Go to SSL/TLS > Edge Certificates.
-
Apply these settings:
- Set Minimum TLS Version to TLS 1.2.
- Enable TLS 1.3
- Enable Always Use HTTPS for seamless security.
10. Use Country-Based Geo Blocking (Optional)
If a DDoS attack is coming from a specific region, you can block traffic from that country temporarily.
Steps to Geo Block:
-
Go to Security > Security rules.
-
Click on the Create Rule button, then on Custom rules.
-
Define your rule settings to block traffic from specific countries:
-
Click on the Deploy button to apply the rule immediately.
11. Remove DNS Records That Reveal Your Server's IP Address
One common mistake is exposing server IP addresses through DNS records. Attackers can bypass CloudFlare and target your server directly if these records are visible.
Steps to Remove or Protect DNS Records:
-
Go to the DNS settings.
-
Review your DNS records:
- Remove unnecessary records like cpanel, webmail, whm, and others that point directly to your server.
- Ensure essential subdomains (e.g.,
www,blog) are proxied through CloudFlare (indicated by an orange cloud icon ☁️). - Avoid exposing your server's IP address in A or CNAME records, unless absolutely necessary.
- Mail Exchange (MX) Records: For high-risk businesses, it may be worth investing in a separate email service (e.g., OX App Suite, Google Workspace, Microsoft 365) to separate your email system from your hosting service. This ensures email delivery security and reduces the potential impact of hosting-related vulnerabilities.
-
Save the changes.
12. Set the Security Level
The Security Level setting determines how aggressively Cloudflare challenges potentially malicious visitors.
Steps to Adjust Security Level:
-
Log in to your Cloudflare Dashboard.
-
Select your website and go to Security > Settings.
-
Choose a security level based on your needs:
- Essentially Off: Minimal protection.
- Low: Less intrusive; ideal for sites with minimal risk.
- Medium: Challenges visitors with suspicious activity (recommended for most sites).
- High: Challenges most visitors not previously verified.
- Under Attack: Forces all visitors to pass a browser verification challenge.
For DDoS-prone periods, use High or Under Attack mode.
13. Adjust the Challenge Passage Duration
The Challenge Passage setting determines how long a visitor remains verified after passing a security challenge (e.g., CAPTCHA or browser check). Shorter durations are more secure but may inconvenience repeat visitors.
Steps to Adjust Challenge Passage:
-
Go to Security > Settings.
-
Locate the Challenge Passage option.
-
Set the duration (e.g., 5 minutes, 30 minutes, or longer):
- Shorter durations: Ideal during active attacks.
- Longer durations: More user-friendly for normal traffic.
14. Enable Browser Integrity Check
The Browser Integrity Check scans incoming requests to identify and block fake browsers or bots that try to access your site.
Steps to Enable Browser Integrity Check:
-
Go to Security > Settings.
-
Toggle Browser Integrity Check to “On”.
This feature helps filter out malicious bots without affecting legitimate traffic.
15. Replace Insecure JavaScript Libraries
Cloudflare can automatically replace outdated or insecure JavaScript libraries on your site with secure, up-to-date versions. This reduces vulnerabilities that attackers could exploit during or after a DDoS attack.
Steps to Enable JavaScript Replacement:
-
Go to Security > Settings.
-
Enable Replace Insecure JavaScript Libraries.
This feature is particularly helpful for older websites using outdated libraries like jQuery.
⚠️ Important: Services or plugins that modify JavaScript or enable Minify can sometimes break website functionality, particularly for dynamic or script-heavy sites. After enabling these settings, test your website thoroughly to ensure everything is working as expected.
By fine-tuning these settings in CloudFlare, you can strengthen your website’s defences against DDoS attacks.
If you need help configuring these settings, feel free to contact CloudFlare or our support team.
Updated by SP on 27/11/2024